This guide explains how to integrate Okta as an identity provider (IdP) for Oxide. It assumes you have an Okta administrator account and access to the Oxide Console with fleet admin privileges.
Create Okta Application
Log in to the Okta Admin Console.
Navigate to Applications and create a new SAML 2.0 app.
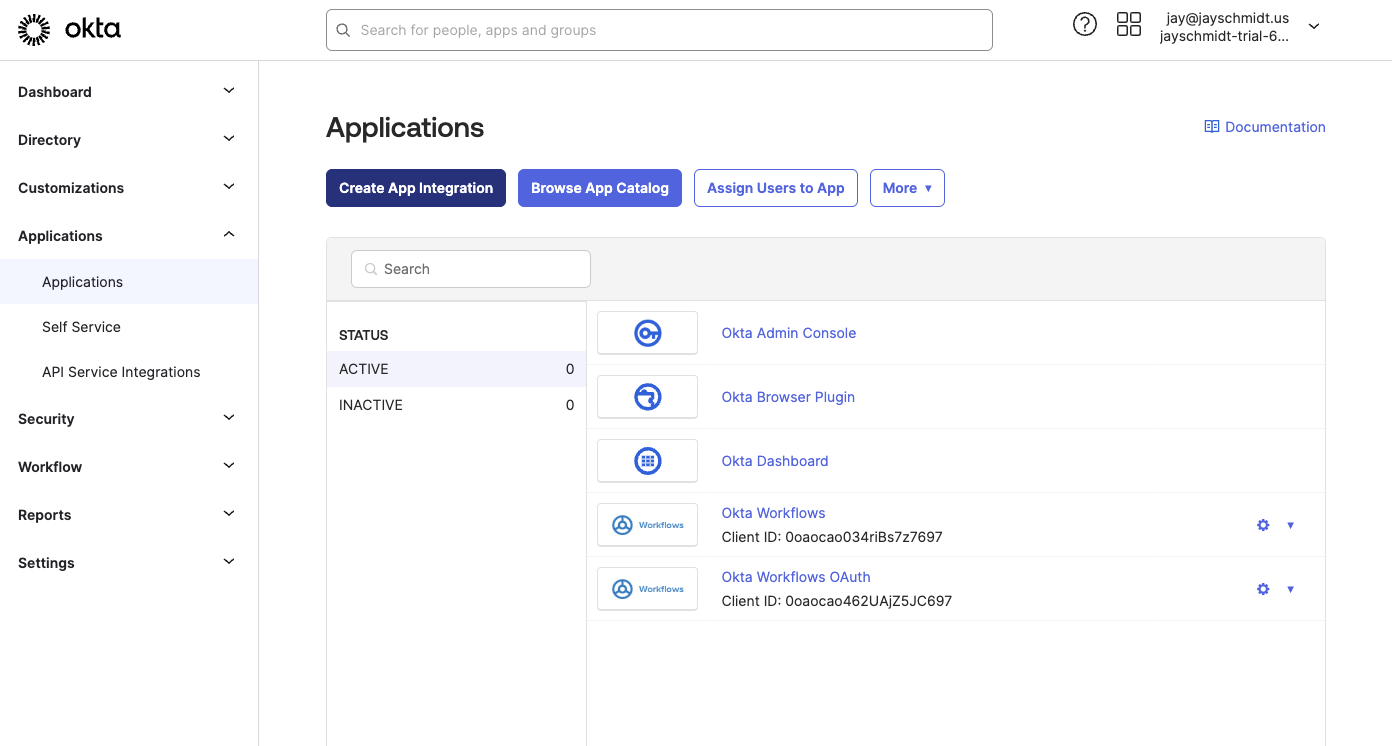
Set the Single Sign On URL (ACS URL in Oxide) to:
https://$siloName.sys.$oxideDomainName/login/$siloName/saml/okta
Set the Audience URI (SP Entity ID) to the same silo name as the one in the URL or another identifier consistent with your environment.
Specify the Name ID format and Application Username as needed.
Configure Group Attribute and Regex Mapping
In the attribute statements, create a group attribute (or your preferred attribute name) that will pass group membership information to Oxide.
Use regex mapping to match only relevant groups (e.g.,
^(admin|user)$).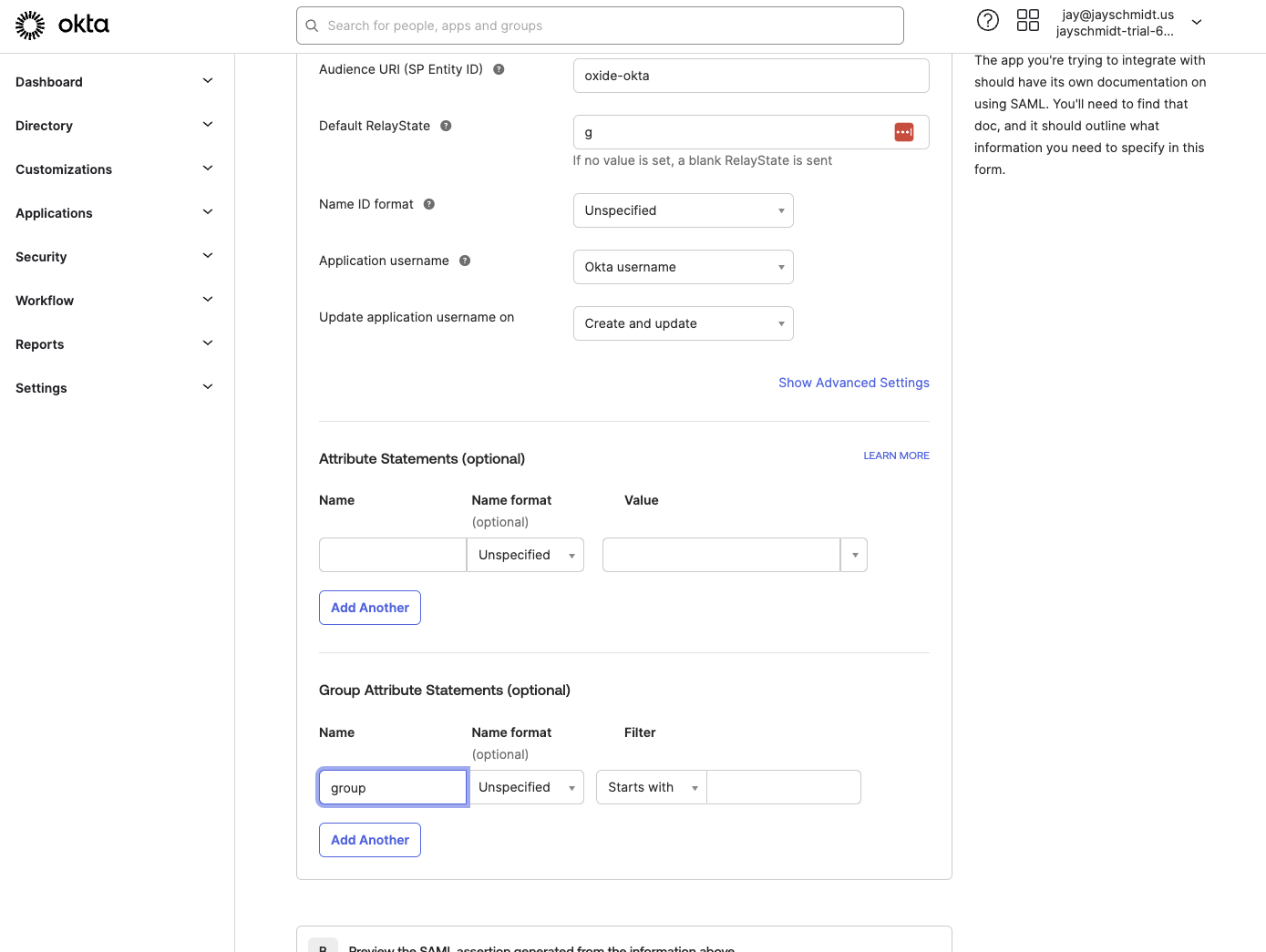
Assign Users and Groups
Assign users or groups to the app.
NOTE: Only users with the group attribute matching your regex will be passed to Oxide.
This ensures Oxide automatically creates groups and assigns users to them.
Export Metadata
Copy the Metadata URL or download the metadata XML from Okta. This will be used to configure the Oxide IdP.
Configure Oxide Silo and Identity Provider
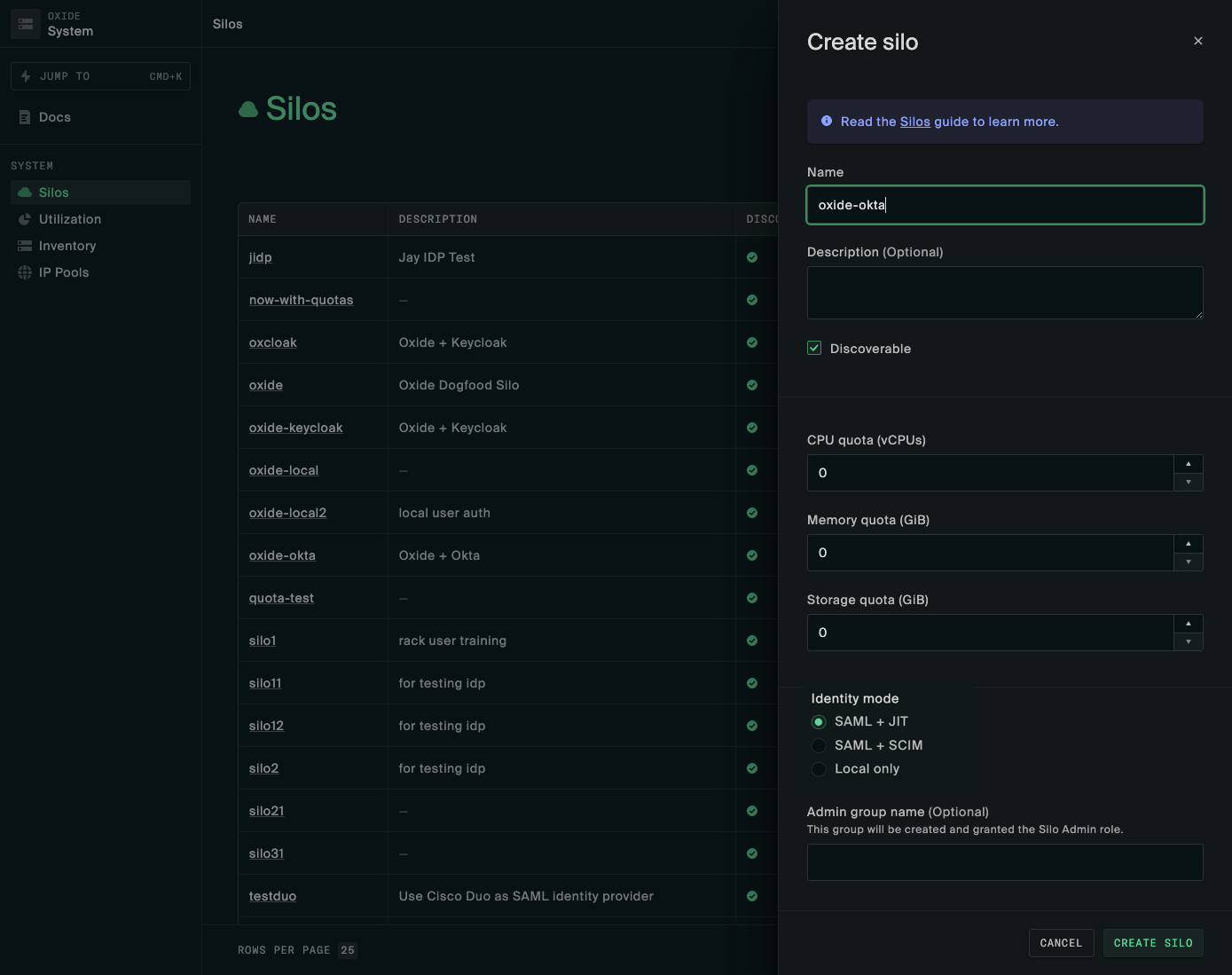
Create Silo in Oxide
In the Oxide Console:
Go to System > Silos and create a new silo.
Silo Name: Must match the name used in Okta.
Admin Group Name: Matches the Okta
groupattribute value for silo admins (e.g.,admin).Add a TLS certificate matching the silo FQDN.
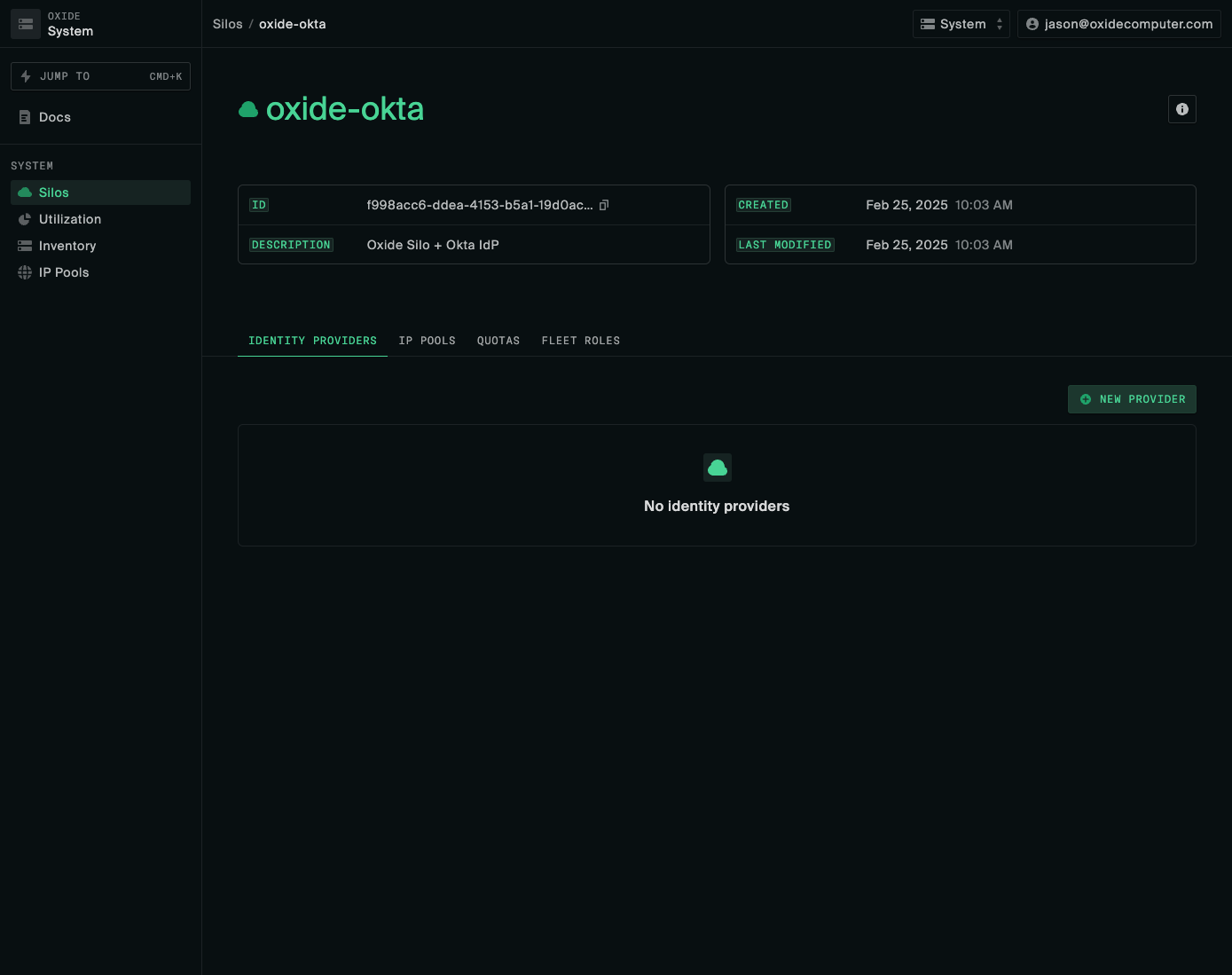
Create Identity Provider in Oxide
In the silo’s Identity Provider tab, click New Provider.
| Field | Okta Value |
|---|---|
Provider Name | "okta" or another descriptive name |
Service provider client ID | Silo name (same as in Okta) |
Entity ID |
|
ACS URL | Auto-generated by Oxide
|
Group attribute name |
|
Metadata source | Use the Metadata URL downloaded from Okta |
Cert/Key files | Provide if using request signing (in DER format) |
Log in to Oxide
After configuration, log in to your Oxide Silo using the Okta SSO button.

User Groups and Access in Oxide
Oxide creates groups and assigns users based on the group attribute sent in the SAML assertion
from Okta.